How To Secure Your Data On A Cell Phone From Google
Android Security
Android security checkup: 16 steps to a safer telephone
Android security doesn't take to be a source of stress. These level-headed steps are all yous need to keep the boogeyman at bay.
Show More
Android security is always a hot topic on these here Nets of Inter — and almost e'er for the wrong reason.
As we've discussed ad nauseam over the years, well-nigh of the missives you read almost this-or-that super-scary malware/virus/brain-eating-boogie-monster are overly sensationalized accounts tied to theoretical threats with practically zilch chance of actually affecting you in the real world. If you look closely, in fact, you'll start to notice that the vast majority of those stories stem from companies that — gasp! — make their coin selling malware protection programs for Android phones. (Pure coincidence, correct?)
The reality is that Google has some pretty avant-garde methods of protection in place for Android, and as long as you lot take reward of those and apply a little mutual sense, you'll almost certainly be fine (yes, even when the Play Store guards skid upwardly and let the occasional bad app into the gates). The biggest threat you should be thinking about is your own security surrounding your devices and accounts — and all information technology takes is 20 minutes a year to make certain your setup is sound.
Take the time now to go through this checkup, then rest easy over the coming the year with the cognition that you lot're in good shape — and that the mean ol' Android malware monster won't be bangin' down your virtual door anytime soon.
Office I: App intelligence
Footstep 1: Look over all the apps and services continued to your business relationship
Yous've probably granted endless apps admission to parts of your Google account over time — which is no big deal in general, but with any apps you're no longer using, it's a smart idea to shut the connections.
[Psst: Want even more advanced Android knowledge? Bank check out my free Android Shortcut Supercourse to learn tons of fourth dimension-saving tricks for your phone.]
Visit this page in Google's security settings to see a listing of everything that's authorized and what exactly information technology can access. If yous encounter anything you don't recognize or that you no longer use, click information technology and then click the bluish "Remove Admission" push button to requite it the kick.
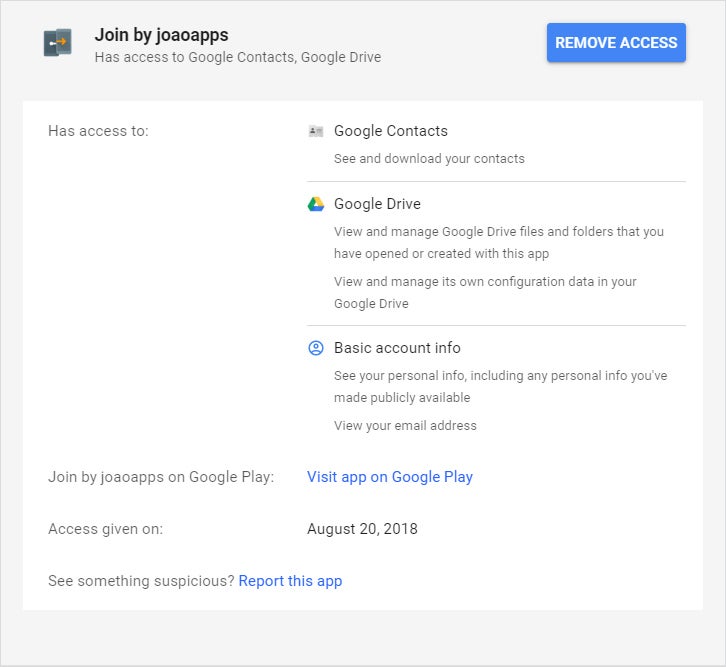 JR
JR And while you're at it, take two minutes to look through the list of apps on your phone and uninstall anything you lot're no longer actively using. It'll eliminate unnecessary windows to different areas of your information,and it'll free up space and cut down on potentially phone-slowing resource utilize, too.
Step ii: Revisit your Android app permissions
Speaking of dusty one-time stuff on your phone, it's all as well easy to grant an app access to some sort of information without giving it much thought during that initial setup process (hello, Facebook!). That's why it'south well worth checking in periodically to remind yourself what permissions the apps on your phone possess — and to see if any of 'em become beyond what seems reasonable or necessary.
With contempo Android versions, just open the Privacy section of your organization settings and look for a line that says either "Privacy dashboard" (starting with Android 12) or "Permission manager" (on other reasonably contempo versions of the operating arrangement). If y'all don't see annihilation like that on your phone, endeavor searching your system settings for the word "permissions" to notice the closest equivalent.
Whatever it'southward called and all the same you get there, you should ultimately finish up facing a collection of categories for all the types of permissions you've granted to apps on your device over fourth dimension. Have a peek through 'em all and see what you find. If you encounter anything that raises an eyebrow, all you've gotta do is tap information technology to revoke the permission.
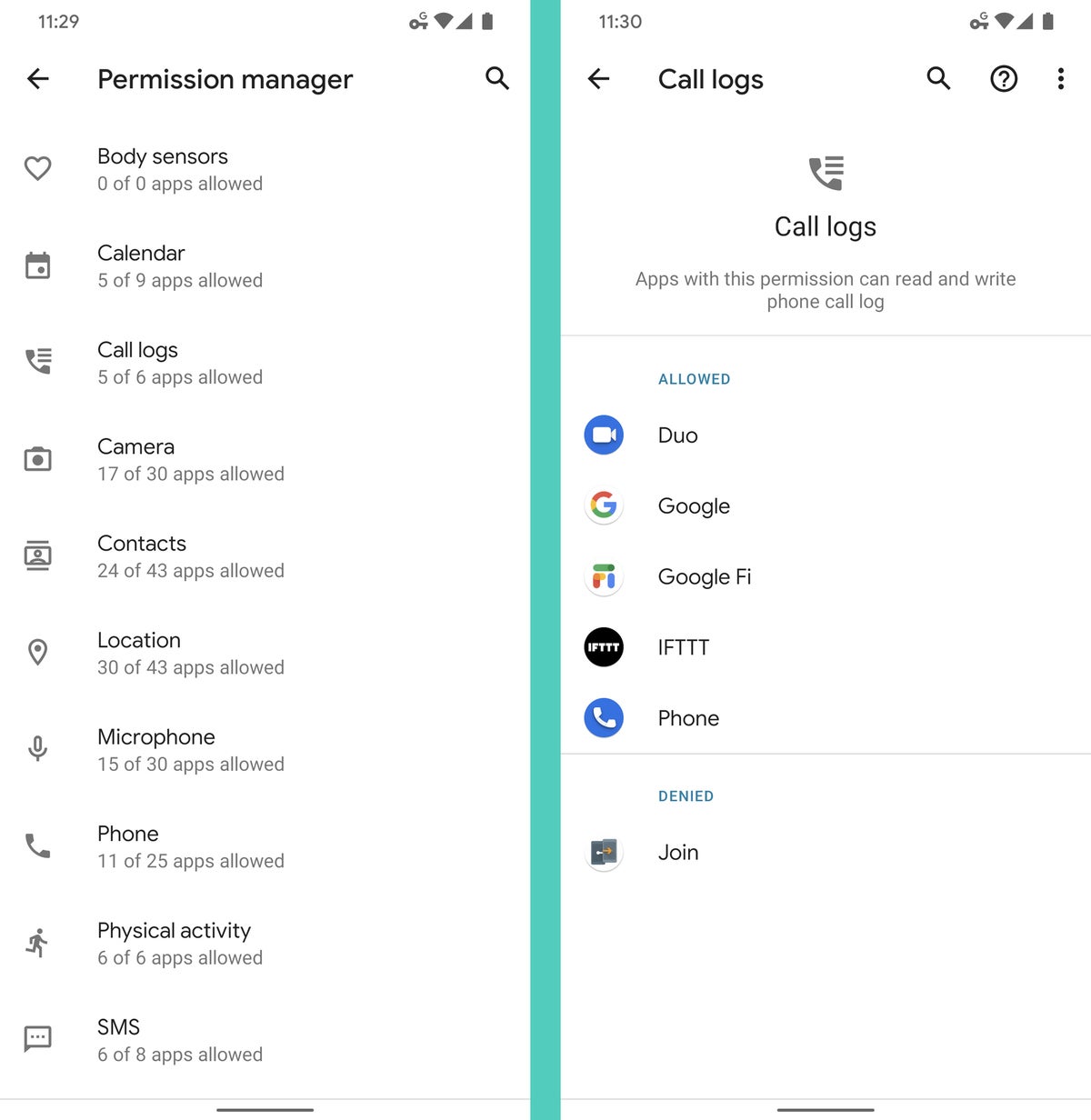 JR
JR And remember, too: With Android 10 and higher, you tin can actually become a step further when it comes to location and allow an app to access that only when you're actively using it. With Android xi and up, you lot can become even more nuanced and grant apps only temporary, case-by-case permissions to admission your location, photographic camera, and microphone. And equally of Android 12, yous can fine-tune an app'southward location access to make information technology just approximate instead of precise, if you like.
Critically, in all of those cases, it's up to you to go through your settings and make the associated changes — especially when it comes to apps you had on your device before the virtually recent Android upgrade reached y'all and the latest options for permission control became bachelor.
Step 3: Verify that you're using Android'southward app-scanning system
Android has long had the power to monitor your device for harmful code or suspicious activity — no tertiary-party apps or add-ons required. And while the system should exist enabled by default on any reasonably current device, it'south a good idea to occasionally ostend that everything's turned on and working the way it should, if for no other reason than to remind yourself that such a system is present and working on your behalf.
So mosey on over to the Security section of your system settings, tap the line labeled either "Google Play Protect" or "App security," then take a peek at the organisation'due south latest activeness. You lot can also tap the gear icon in the upper-right corner of the screen and confirm that all available toggles are on and in the active position.
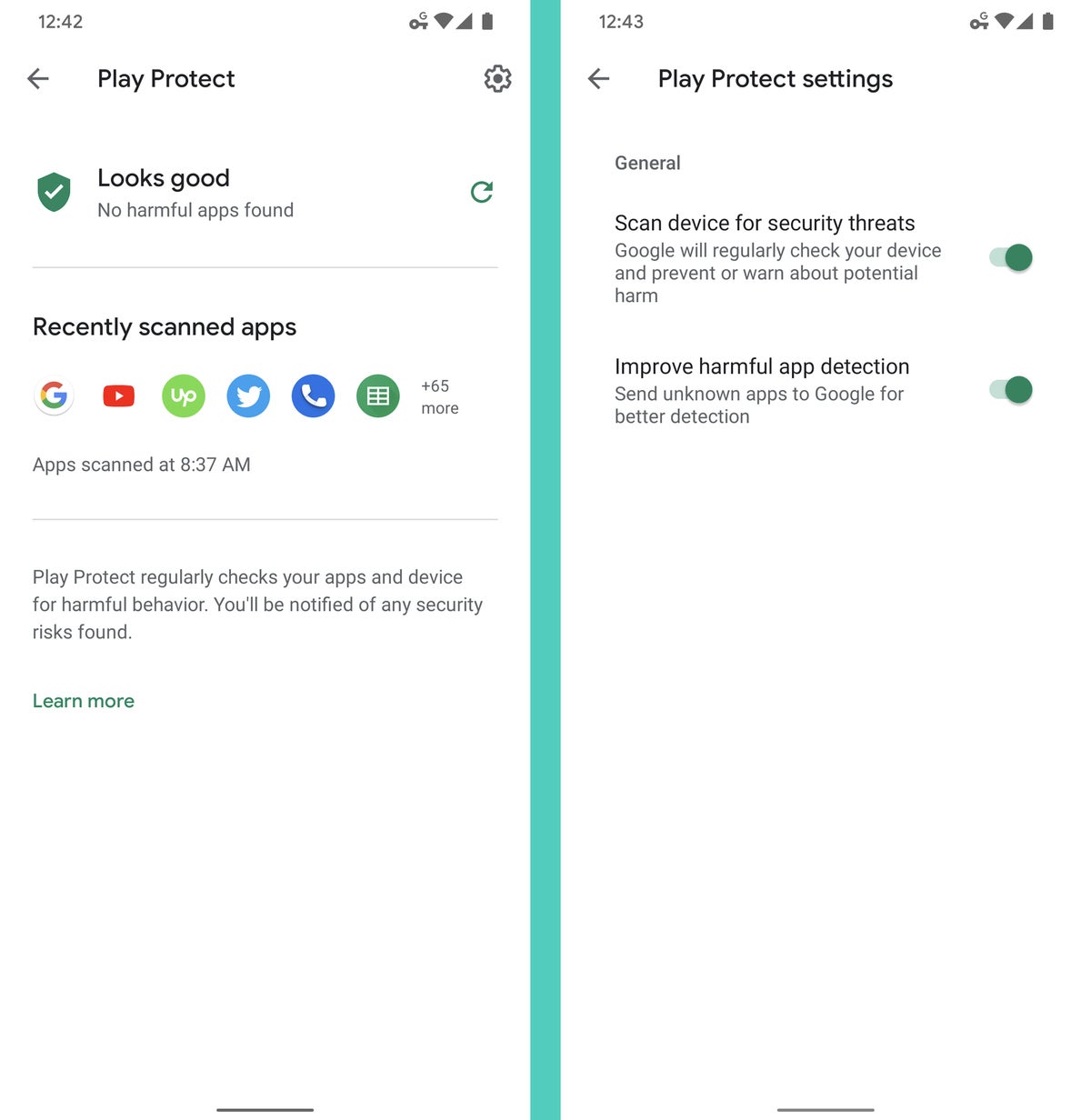 JR
JR That'll allow Android's app verification system to proceed an eye on all apps on your device, even afterward they're installed, and make sure they don't practise anything dangerous. The scanning will run silently in the background and won't ever carp you unless something suspicious is found.
Odds are, you lot'll never fifty-fifty know it'southward there. But information technology's a valuable piece of protection and peace of mind to accept, and it's a adept thought to keep it in the back of your listen that it'southward present.
Step four: Appraise your app-downloading IQ
If y'all're reading this column, I probably don't need to tell you this — simply I volition, anyway: While we're thinking about the subject of Android security, have on a teensy scrap of responsibleness and commit to letting common sense guide your app-downloading decisions.
Look, permit's not child ourselves: Google's security mechanisms are invariably gonna fail on occasion. At that place's no getting around that. Just even when a shady app makes its style into the Play Store, all it typically takes is the tiniest shred of awareness to avoid having information technology affect you in any way.
Just as yous exercise when browsing the web from a computer, look at something before you download it. Look at the number of downloads and the overall reviews. Call up near what permissions the app wants and whether you're comfortable with the level of access it requires. Click the proper noun of the programmer, if yous yet aren't sure, and come across what else they've created. And unless yous really know what you're doing, don't download apps from random websites or other unestablished tertiary-party sources. Such apps will nonetheless be scanned by Google'due south on-device security system earlier they're installed, but your odds of encountering something shady are significantly greater out in the wild than within the Play Store.
(Your Android device won't let you download apps from unknown sources by default, by the style, so if you always attempt — even inadvertently — you'll be warned and prompted to authorize that specific form of not-Play-Shop download. Apps on Android volition never magically install themselves without your explicit dominance, nor will they always be able to access any sensitive sensors or areas of data unless you grant them the associated permission.)
Generally, all information technology takes is a 10-second glance to size something up and run across if information technology's worth installing. With all due respect to the dodos of the world, it doesn't have a rocket scientist to stick with reputable-looking software and avert questionable creations.
Part Two: Passwords and authentication
Step 5: Double-check your security basics
A quick no-brainer that'southward of import to mention: If yous aren't using biometric security and/or a PIN, blueprint, or password on any of your devices, start doing it. Now.
Talk to any security expert, and y'all'll hear the same thing: The near likely cause of a security failure is simply a failure on your behalf to secure your stuff. You lot are the weakest link, as the absurd kids said 15 to xx years ago.
Embarrassingly dated pop culture references aside, think about it: If your phone has no passcode protecting it, all of your information is just out there and waiting for the taking anytime yous exit the device unattended (intentionally or otherwise). That includes your email, documents, social media accounts, and entire photo drove (aye, fifty-fifty those pictures — hey, I'one thousand not here to judge).
The best office: Android makes it hassle-free as can be to go along your devices secure. The software's Smart Lock function allows you to automatically leave your telephone unlocked in a variety of preapproved "prophylactic" atmospheric condition — like when y'all're at abode, when a specific trusted Bluetooth device is connected, or fifty-fifty when the telephone is beingness carried in your pocket. That means the extra security shows up only when information technology's actually needed, and you lot don't accept to mess with it the residue of the time.
You can find and set up Smart Lock in the Security section of your system settings, often subconscious behind an "Advanced settings" option — or if all else fails, simply search your organisation settings for the term to turn up the available options.
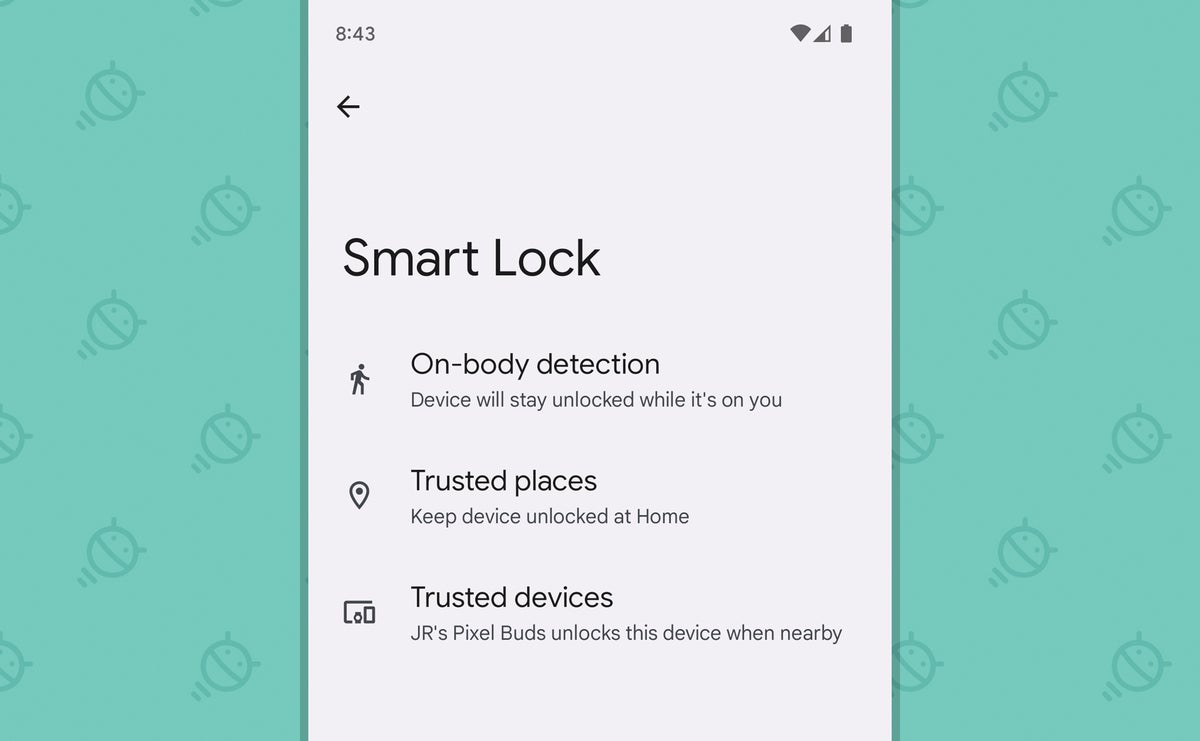 JR
JR Plain and simple, there's no excuse to leave your stuff unprotected. Caput into the Security department of your device's settings to go started this second, if yous haven't already.
Step 6: Peek in on your saved Smart Lock passwords
Speaking of Smart Lock, one of the less often discussed parts of Google's security system is its ability to save passwords for websites and apps accessed via your mobile devices. As part of your annual checkup, glance over the list of saved passwords Google has for your account and so you'll know what'due south in that location and what, if whatever, of your credentials have been compromised (which Google volition patently warn you lot about at the top of that very same screen).
While you lot're at it, have a few seconds to remove any dated items that are no longer needed and don't vest. Your future self volition thanks.
Step 7: Assess your password direction system
Google'southward saved password system is better than nothing, but you'll get stronger security assurances, more than advanced and useful features, and broader support for in-app password filling by using a defended password management service.
Plenty of commendable options are available, with broadly recommended favorites including LastPass, 1Password, and Bitwarden. Whatsoever such reputable service volition work equally well on the desktop and even on iOS, and well-nigh have broadly similar levels of security with the primary differences being cost, actress features, interface, and the resulting overall user experience.
If you lot aren't using one of those services, now'south the time to start. And if yous are already using such a service, take a few minutes now to peek into the app's settings and make certain you lot're taking advantage of all the on-device protection it offers. With LastPass, for example, y'all should confirm that options to lock the app automatically and whenever it's idle for more than a few minutes are active. Y'all should make certain the app requires a Pivot or biometric authentication to unlock. And y'all should confirm that the app is fix up for offline access, in example the need ever arises. (All of those options are in the Security section of LastPass's settings.)
Like Google, nigh expert password managers besides now provide an selection to analyze all of your passwords and identify whatsoever that would be advisable to change — ones that are duplicated or otherwise not as strong as they could exist. That'due south some other smart thing to cheque up on equally role of this annual audit.
Step viii: Evaluate your two-factor hallmark state of affairs
A single password isn't plenty to protect an of import account these days — especially one as wide-reaching and valuable as your Google account. Two-cistron authentication makes it then that you take to put in a special time-sensitive code in addition to your password anytime y'all try to sign in. That significantly increases your level of security and decreases the odds of anyone ever being able to break in and access your personal data, since they'd demand both knowledge of your password and the concrete presence of your lawmaking-generating device (most likely your phone) to practice it.
If you don't yet have two-factor authentication enabled for your Google account, head over to this site to get started. And don't finish with just Google, either: Look into enabling two-factor hallmark on whatever service that offers it, including your password manager, your social media accounts, and any non-Google cloud storage services that you use. Once you have things configured everywhere, you lot'll rely on either your phone itself to serve every bit a security key or an app like Google's Authenticator to generate single-use codes from your phone. Yous can also utilise a 3rd-political party alternative like Authy, which is more characteristic-rich than Google's Authenticator and can run on multiple devices.
Speaking of Authy, if you're already using that for two-factor authentication, open up the app correct now and head into the My Account section of its settings, then tap "App Protection" and confirm that you're using a PIN or fingerprint for protection. Then pop over to the Devices section of the same settings menu to cheque up on exactly what devices are authorized to access the app. Remove any that are dated and no longer in utilise.
If you really want to go along your account secure, Google also offers a souped-upwardly choice called Advanced Protection. It requires you to purchase concrete security keys and so utilize those anytime you sign into your Google account. It also severely limits the ways in which 3rd-party apps tin can connect to your business relationship. That sort of elevated and locked-downward setup probably won't be sensible for most folks, but if yous feel similar you need the extra protection, you tin learn more and enroll hither.
Step nine: Optimize your lock screen security
Your lock screen is the guard of your Android device's gate — and there are a few things you tin do to beef upwardly its musculus and make sure information technology's fully prepared for the job.
First, think about the types of notifications you get and how much of that info yous want to exist visible on your lock screen — since anyone who gets their hands on your phone could easily see all that information. If yous tend to get sensitive messages or merely want to step upwards your security and privacy game a notch, head into the Display department of your organisation settings and select "Lock screen" or "Lock screen display." (On some devices, you might need to look in either the Security section or within a special "Lock screen" section of the settings to observe a similar option.)
At that place, y'all'll observe tools for controlling precisely what volition and won't be shown in that pre-authentication area as well as for creating a security-minded message that'll always appear on your lock screen — for instance, something like: "If institute, please call Joe T. Schmo at 333-222-1111." You could fifty-fifty consider adding an emergency contact into your settings and so using the lock screen message to direct people to that information.
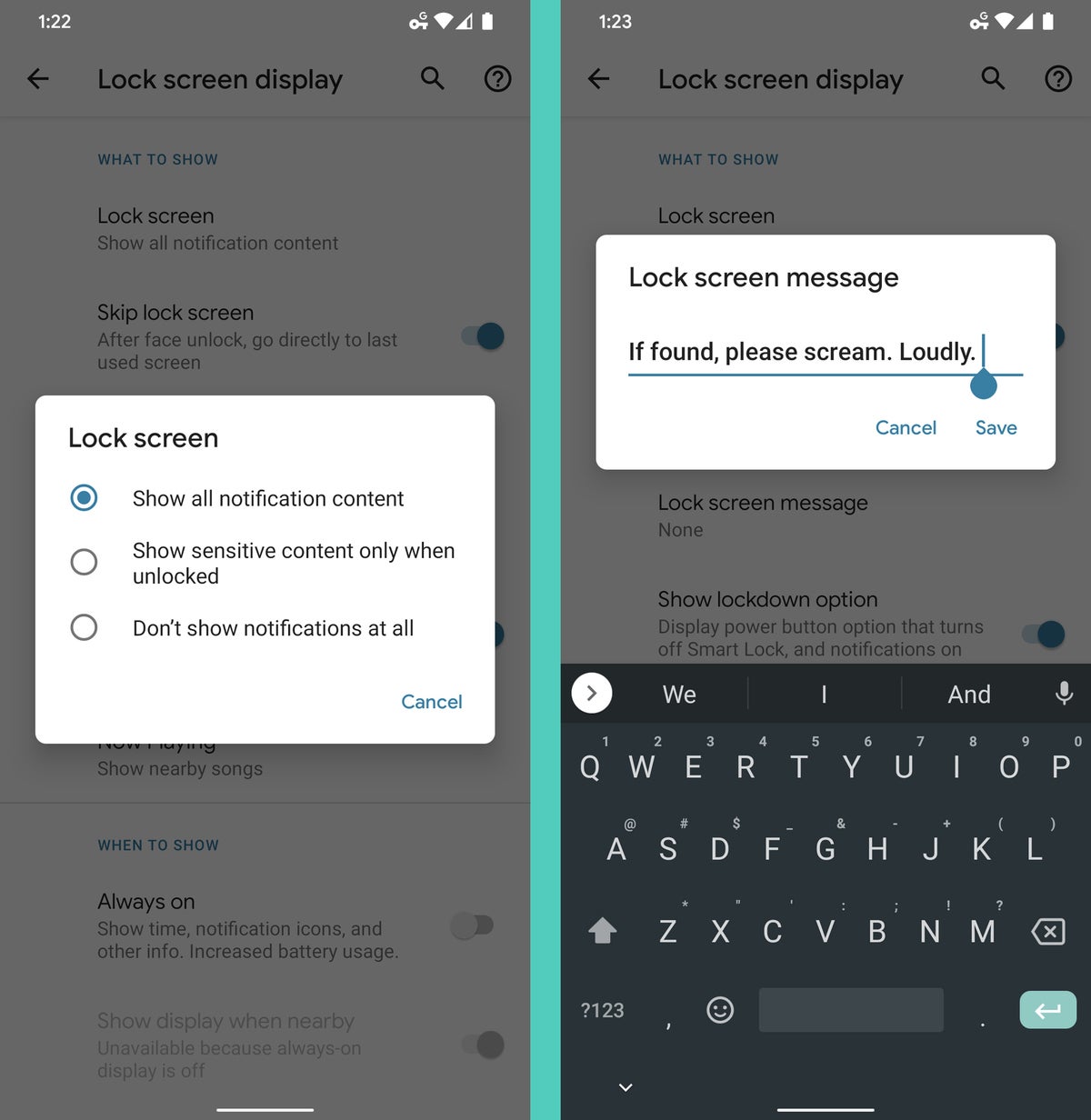 JR
JR And finally, if your phone is running Android ix or higher, an option called lockdown mode is well worth your while to actuate. One time enabled, it gives you lot a fast way to lock your phone downwards from all biometric and Smart Lock security options — pregnant simply a design, Pin, or password could get a person past your lock screen and into your device.
The thought is that if you were ever in a situation where you thought you might be forced to unlock your telephone with your fingerprint or face — be it by some sort of law enforcement agent or merely past a regular ol' hooligan — you could activate the lockdown mode and know your data couldn't be accessed without your explicit permission. Even notifications won't show up on your lock screen when that mode is activated, and that heightened level of protection will remain in identify until you manually unlock your telephone (even if the device is restarted).
At that place's only one take hold of: On some devices, information technology'southward up to yous to enable the option ahead of time in order for it to be available. But doing so takes only a couple of seconds: In that aforementioned "Lock screen" section of your system settings, simply activate the toggle side by side to "Bear witness lockdown option" — or tap "Secure lock settings" and so "Show Lockdown option," with Samsung devices — and that'south it. (If y'all don't see whatever such option at all, odds are, y'all're using a recent enough Android version that it'south merely on and enabled by default.)
Then, if the need always arises, but remember this: In your phone's power carte du jour, along with the regular options for restarting and shutting downwardly your device, yous'll always find a button to activate that "Lockdown" function. Hopefully, you'll never need information technology — but now you're ready in case you do.
And with that, guess what? You lot're more than halfway done with this annual checkup. Non besides painful so far, right? Only six more steps to become...
NEXT Page: Device admission and final considerations
How To Secure Your Data On A Cell Phone From Google,
Source: https://www.computerworld.com/article/3012630/android-security-checkup.html
Posted by: jimenezenwhat.blogspot.com


0 Response to "How To Secure Your Data On A Cell Phone From Google"
Post a Comment